Third-Party Fraud
Explore third-party fraud in lending, where criminals exploit stolen identities and digital footprint analysis helps uncover deception.

Explore third-party fraud in lending, where criminals exploit stolen identities and digital footprint analysis helps uncover deception.

Every year, banks and fintech companies lose millions of dollars due to fraud. At the same time, a survey conducted by Alloy indicates losses of up to $10 million in more than 30% of financial institutions.
There are several types of financial fraud, including first, second, and third party frauds. Understanding the fundamental differences between them is the first step toward effective fraud prevention.
In the lending sector, third-party fraud refers to a situation where a criminal takes out a loan using the personal data of a real individual without their knowledge. In other words, a real person becomes a victim of a fraudster.
Alongside this fraudulent scheme, there are other known as first-party fraud and second-party fraud.

In the first case, criminals take out a loan in their name but have no intention of repaying it.
In the second case, a third party knowingly permits their data to be used in unlawful acts, making them an active participant in the crime.
Year after year, more and more methods of deception appear, which are actively used by fraudsters. Let’s take a look at the most common types of third-party fraud.
Fraudsters use someone else’s personal information to open accounts and submit loan applications.
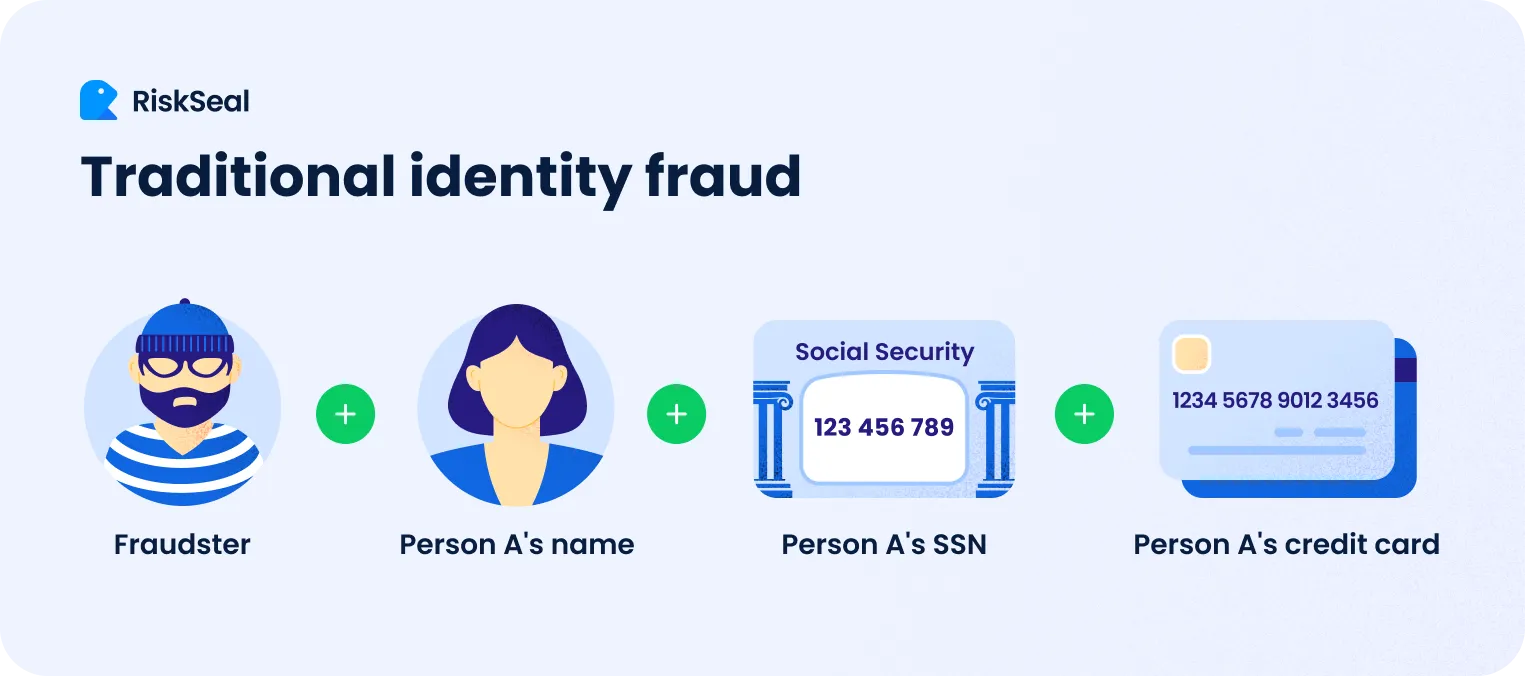
There are various ways to obtain this information. For example, through phishing and social engineering, a person is tricked into revealing confidential data.
Fraudsters gain unauthorized access to someone else’s accounts to carry out fraudulent transactions, including taking out loans.
This is one of the most widespread third-party fraud schemes. It involves creating a fake identity by combining real and fabricated information.

For example, criminals might use an existing Social Security number, but pair it with a fake name and phone number.
In addition to the wide range of third-party fraud techniques, there is also an impressive variety of financial institutions where criminals can obtain loans.
These can include lenders of different scales, from large banks to local P2P platforms.
In the first case, third-party check fraud is common.
In the latter, P2P fraud is implied. This refers to fraudulent activity on peer-to-peer lending platforms, where people borrow and lend money without traditional financial intermediaries.
To increase the effectiveness of fraud prevention, lenders should turn to alternative data providers, who enrich risk models with non-traditional insights.
These providers use non-traditional sources of information to build a comprehensive financial profile of the applicant. Among such sources, digital footprint analysis is rightfully recognized as the most informative.
It enables the analysis of behavioral and technical indicators of a borrower online. For example:
Thanks to this extensive range of data, fraud prevention with digital footprint analysis demonstrates high effectiveness.
A credit institution can detect inconsistencies and anomalies that indicate a high level of borrower risk.
Among the suspicious indicators that may be interpreted as signs of fraud are:
1. Absence of a digital footprint. According to statistics, the average user has 6-7 online accounts. Therefore, a complete lack of registrations on digital platforms should serve as a warning sign for the lender.
This fact may suggest that the applicant’s profile was recently created, quite possibly to deceive yet another credit institution.
2. Mismatch between region, device, and user behavior. For example, digital credit scoring may reveal that the user connected from a region that does not match the residential address specified in the application.
Another example - the applicant may log in using an Android device, while they had previously always used iOS.
Suspicion may also be raised by a sudden change in spending behavior: large purchases, unusual money transfers, and so on.
3. Signs of a mass automated attack. This involves the use of bots, scripts, or malicious software to quickly submit multiple loan applications.
Such attacks are often carried out using stolen or synthetic identities, which directly contribute to synthetic fraud credit losses. Detecting them can be extremely difficult without real-time identity verification and other capabilities of advanced scoring systems.