How to Estimate the Age of an Email Account: Five Non-Obvious Approaches
Learn five different methods on how to discover the age of an email account.

The age of an email account is a valuable type of alternative credit data. It plays a crucial role in email risk analysis, helping enhance risk management in lending organizations.
This is supported by statistics from Banking Exchange. The source claims that 30% of fraudsters use disposable email addresses — mailboxes created for short-term use with a specific purpose. Typically, such addresses are registered right before contacting a credit organization.
At RiskSeal, we specialize in assessing potential borrowers through digital footprint analysis. This includes helping credit organizations assess solvency with email address verification for loan approval.
Pinpointing an email account's registration date can be extremely challenging. However, we have five indirect methods to achieve this.
Approach #1. Domain registration date
If it's a custom domain email (like name@company.com), you can check the domain's registration date using WHOIS databases.
This won't tell you when the email address was created, but it can give you the earliest possible date since the email couldn't have been created before the domain was registered.
In the image below, you'll find a snapshot of the riskseal.io domain details, highlighting the creation date: September 28, 2022.

Approach #2. Social media or online services
People sometimes use their email addresses to register for various online services, including social media.
If the email is connected to such accounts, the date of the earliest activity on these platforms might provide a clue.
In the screenshot below, we can see that the Intro section of a Facebook user indicates that the date of their registration in the social network is January 2010. Therefore, we have reason to believe that the e-mail with which they registered on Facebook was created no later than January 2010.

Two important points should be noted:
- This is not an absolute indicator. Users might initially register in a social network with one email but later change it. Consequently, the existence of the email is not guaranteed once it is registered in the social network, even though the likelihood of this scenario is relatively high.
- Verifying the email associated with a social network account can be challenging. One method involves importing email contacts directly from Facebook into your selected email account provider.
Approach #3. Analysis of breached data
Typically, a data breach is an incident wherein information is stolen or taken from a system without the knowledge or authorization of the system's owner. There are public services that collect information about data breaches and allow customers to see if it has been part of any known data breaches.
If the email address appears in one of these databases, it was likely active at the time of the breach. This can provide the earliest possible date for the account's creation.
Such information can be found, for example, on the service HaveIBeenPwned.com.
Our email lookup service from RiskSeal also provides analytics on this aspect. In the following screenshot, you can observe the details that the platform furnishes regarding data breaches.

Approach #4. Cross-referencing with other information
If you also have access to other pieces of information about the email account (like previous interactions or social media sign-ups), you can cross-reference these with the breach data to get a more accurate picture of the account's age.
This is an additional check that increases the chances of finding the correct email address creation date.
However, it's important to note that there is no absolute guarantee of success in this regard either.
Approach #5. Google Dorking
Google Dorking is a method for uncovering information on public servers through search engines. To find the creation date of an email using Google Dorking, you can use various search operators.
It's crucial to remember that the use of Google Dorking should comply with laws and ethical standards and should not compromise the privacy or security of other users.
How the age of an email influences risk management
The age of an email account is a valuable type of alternative credit data. It can help enhance risk management in lending organizations.

Recently created email addresses can serve as red flags for online lenders, while older accounts with a history can significantly increase a borrower’s chances of obtaining a loan.
Here is how lenders can utilize this information:
1. Risk assessment. Based on the results of an email address check, lenders can adjust their credit scoring processes. For example, it may be reasonable to scrutinize an applicant with a newly created email address more closely.
2. Borrower identity verification. Older email accounts are more likely to belong to legitimate users. This is because digital traces, such as profiles registered with the email or data leaks, are almost impossible to fake.
3. Detection of potential fraudsters. Criminals often use disposable email addresses to carry out fraudulent schemes. This allows them to hide their true identity and avoid accountability.
4. Pre-KYC checks. Utilizing an advanced email lookup solution enables lenders to filter out unreliable borrowers even at the application stage. This helps save costs on conducting Know Your Customer procedures for such applicants.

5. Enhancing user experience. Email address checks are rapid processes. They enable lenders to deliver credit application results in just a few minutes. Thus, borrowers don’t have to wait weeks for a decision. This improves the user experience and increases customer loyalty to lending organizations.
How fraudsters fake “old” emails and why digital footprints still expose them
Fraudsters know lenders flag newly created email accounts, so they’ve adjusted their playbook.
Instead of relying on obvious throwaway inboxes, they now manufacture aged-looking identities designed to pass basic verification.
This makes email age useful only when interpreted alongside the broader digital footprint.
A lender must be able to separate the appearance of maturity from the reality of behavior. That means evaluating email age within context, not as a single deterministic signal.
1. Hijacked long-standing accounts
Credential breaches give attackers access to real inboxes that have been active for years. On the surface, these accounts look perfectly legitimate, which is why age alone can be misleading.
The indicators of takeover show up elsewhere:
- abrupt device changes
- impossible login locations
- unusual behavioral patterns
A healthy account has rhythm. A compromised one doesn’t.
2. Purchased or artificially “warmed” aged emails
Fraud marketplaces sell older accounts with fabricated activity histories. Fraudsters then run automated warm-up scripts to imitate real usage and create the illusion of stability.
These accounts typically collapse under deeper inspection.
There is no matching phone or identity history, no cross-platform life, and no behavioral cohesion across systems.
The email is old, but the identity supporting it is hollow.
3. Thread-injection and clone impersonation
Some attackers embed themselves into legitimate conversations or recreate old message threads to mimic continuity.
This tactic works well against human reviewers, especially in high-volume queues.
Digital footprint analysis exposes the disconnect. The thread can look consistent, but the supporting signals, such as login routes and usage patterns, move abruptly in ways real users don’t.
Why a mature inbox isn’t enough to prove you’re real
Even when an inbox carries years of apparent history, the surrounding ecosystem tells the real story.
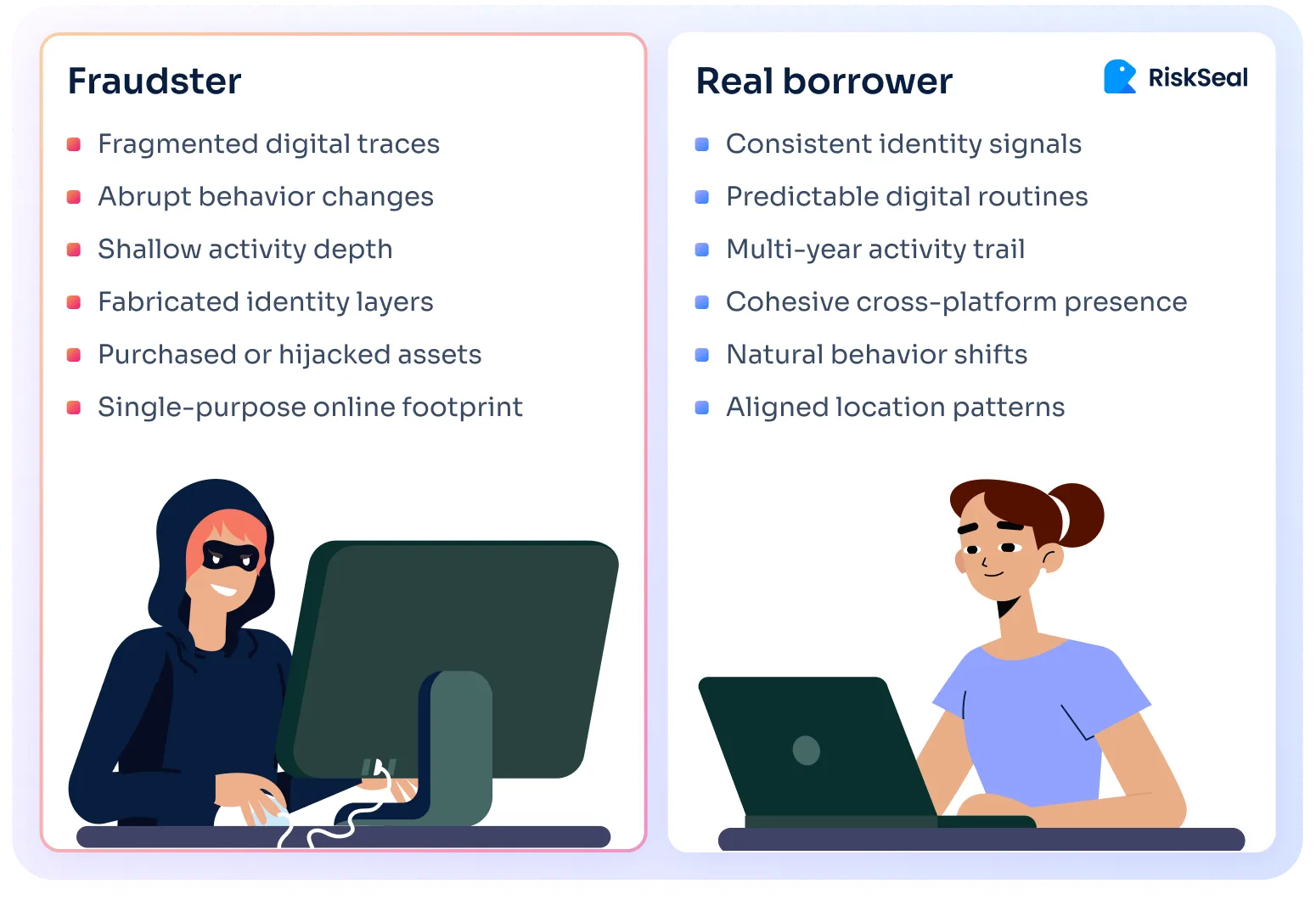
Genuine digital identities evolve gradually and consistently, with signals that reinforce each other over time. Several patterns tend to align in legitimate cases:
- Long-lived phone and email, not just contact details created right before applying
- Stable subscription and e-commerce trail, not just a handful of isolated transactions
- A consistent presence across multiple platforms, not just a single online account
- Coherent location and IP reputation, not just one clean login event or data center trail
These signals develop over years, not weeks. And they tend to move in parallel, even when people relocate, switch devices, or travel frequently.
Synthetic or manipulated identities break that coherence. The email may look mature, but the broader footprint shows abrupt changes, shallow activity depth, or incompatible behaviors.
Fraudsters can buy an old inbox. But they cannot recreate the timeline that makes an identity authentic.
Advanced email lookup capabilities for lenders
Innovative email lookup tools provide lenders with access to a wide range of applicant data.

At RiskSeal, knowing only the borrower’s email address, we provide our clients with the following information:
- Information about the email account owner. This includes personal details (first name, last name), associated phone numbers, and other email addresses.
- Online profiles registered with the email. These can include accounts on social media, gambling sites, e-commerce platforms, etc.
- User photos. These can be compared with one another to identify similarities or differences. If the lending organization’s conditions require a selfie, it can also be matched with the found avatars.

For more details about the role of email address checks in credit risk management, refer to our previous article.
How RiskSeal can help
Determining the age of an email account can be a complex process. The approaches, such as analyzing public data sources or inferring from data breaches, provide some level of insight but may lack precision.
To achieve the best results, we at RiskSeal analyze the email addresses of potential borrowers using the following variables:
- Email age
- Deliverability verification
- Digital and social profile registrations
- Domain data analysis
- Data breaches
- Disposable domain identification

As a result, our clients receive over 400 data points and can assess the authenticity of the email address. This is made possible, in part, by data on its age and registrations across more than 200 social and online platforms.
Feel free to contact us for additional details on locating digital footprints.

Download Your Free Resource
Get a practical, easy-to-use reference packed with insights you can apply right away.

Download Your Free Resource
Get a practical, easy-to-use reference packed with insights you can apply right away.




FAQ
How reliable is the domain registration date in estimating the email account's age?

The domain registration date serves as the earliest possible date for the email account creation. However, it doesn't pinpoint the exact email account creation date. Keep in mind that the email could have been created after the domain registration date.
Can social media activity be a definitive indicator of an email account's age?

Social media registration dates can provide clues about the email's creation date. However, changes to email addresses on social media accounts and difficulty in verifying the linked email pose challenges. It's a useful hint, but not foolproof.
How accurate is the information obtained from data breach analysis?

If an email appears in a data breach database, it suggests the email was active during the breach. This gives the earliest possible date for the account's creation.

.svg)

.webp)



.webp)