How Risk Teams Use IP Intelligence to Reduce Defaults
Discover how IP intelligence enhances financial risk assessment by revealing user identity, location, and behavioral signals.
.webp)
Scams are rising fast across financial services.
In 2024, banks saw a 61% increase in scam activity. 35% of fintechs reported a 10-50% rise in fraud attempts, too.
Here are the most common scam types across financial institutions:
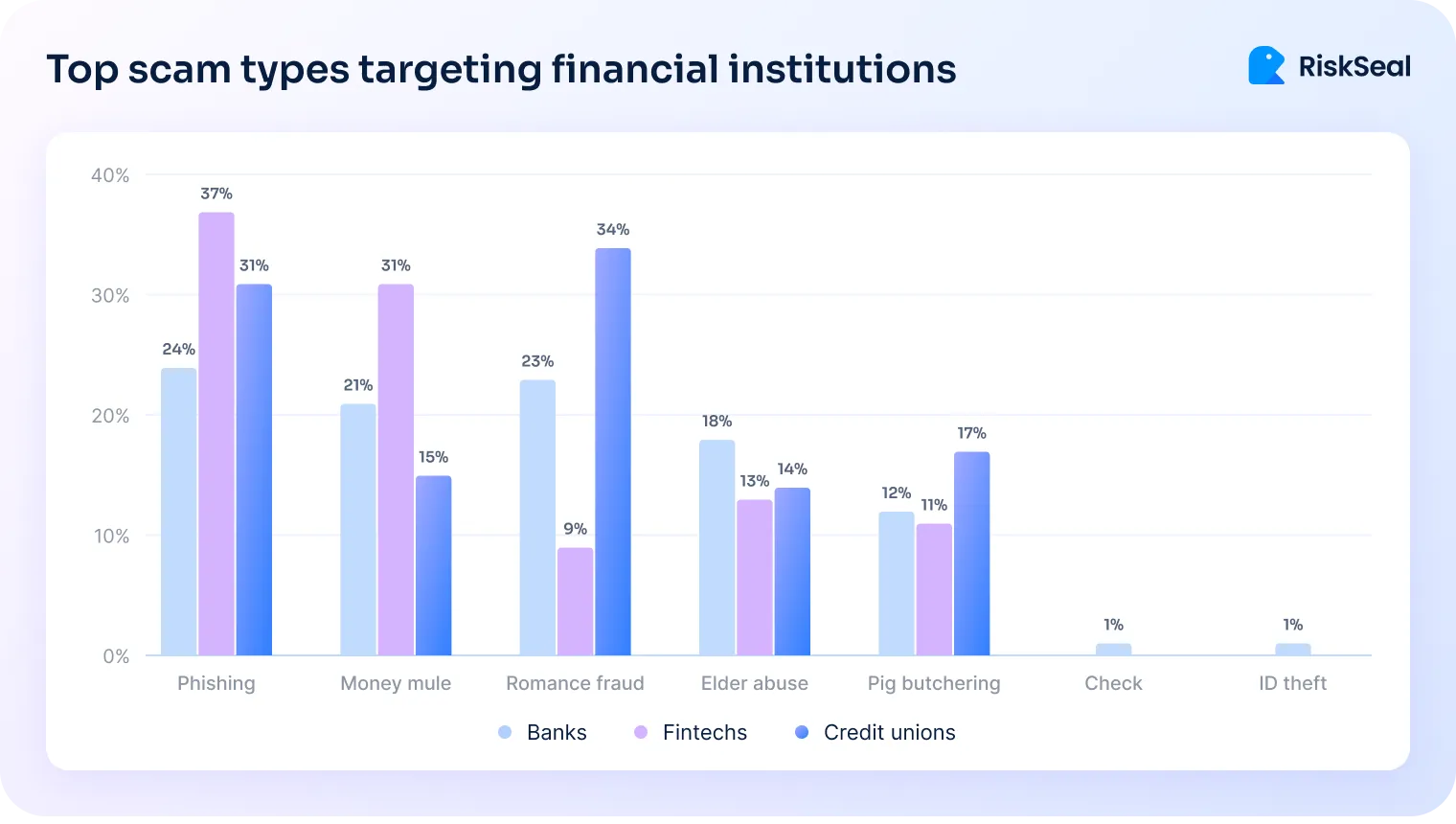
This rise shows that traditional checks alone can't catch emerging threats. Risk teams need early signals to flag suspicious behavior before onboarding starts.
That’s where IP intelligence comes in. Here’s how to use it effectively.
What IP address location lookup really tells lenders
IP analysis for risk insights helps lenders assess creditworthiness, especially when traditional data is missing or limited.
Here’s what you can learn from IP data:
IP insights for applicant verification
An IP address gives a general idea of where the applicant is. It can show the country, region, city, and postal code. This helps confirm if the person is applying from the place they claim.
IP data also shows which internet service provider (ISP) is being used. Sometimes, it even reveals the name of the company or hosting provider behind the connection. This helps spot unusual activity.
For example, someone applying for a personal loan might be using an IP linked to a business, a server, or a location that doesn’t match their application.
Such mismatches can be signs of fraud, fake identities, or the use of tools to hide location.
The type of IP also matters. Here's a quick breakdown:
Privacy and anonymity signals
Some applicants use tools to hide their real location or identity – VPNs, proxies, Tor, or Apple Private Relay. While not always malicious, these tools reduce transparency and can increase risk.
To help evaluate trustworthiness, many systems attach reputation and fraud indicators to IPs.
Here's a snapshot of common signals:
These checks help avoid approving applications tied to known high-risk behaviors.
Behavioral patterns and risk levels
IP address lookup software can also offer real-time behavioral insights. Unusual spikes in request volume, odd local time of access, or mismatches with expected device types may indicate risk.
Some signals are especially useful in fraud detection and onboarding:
Technical metadata, like ASN, reverse DNS, CIDR subnet, and IP version (IPv4 or IPv6), adds valuable depth for systems evaluating traffic in real time.
Combined, these signals make IP risk assessment a powerful tool in credit risk evaluation. When properly integrated, it can help flag suspicious behavior early. That's why platforms like RiskSeal include it as part of their data scoring stack.
Using IP intelligence in credit decisioning
IP data isn’t just about blocking fraud. It also improves lending decisions, especially when traditional data is limited or unreliable.
Here are three key ways IP address analysis in credit risk adds value to workflows.
#1. Enhance creditworthiness assessments with IP geo lookup
Many applicants don’t have formal credit histories. But IP data can still offer useful signals.
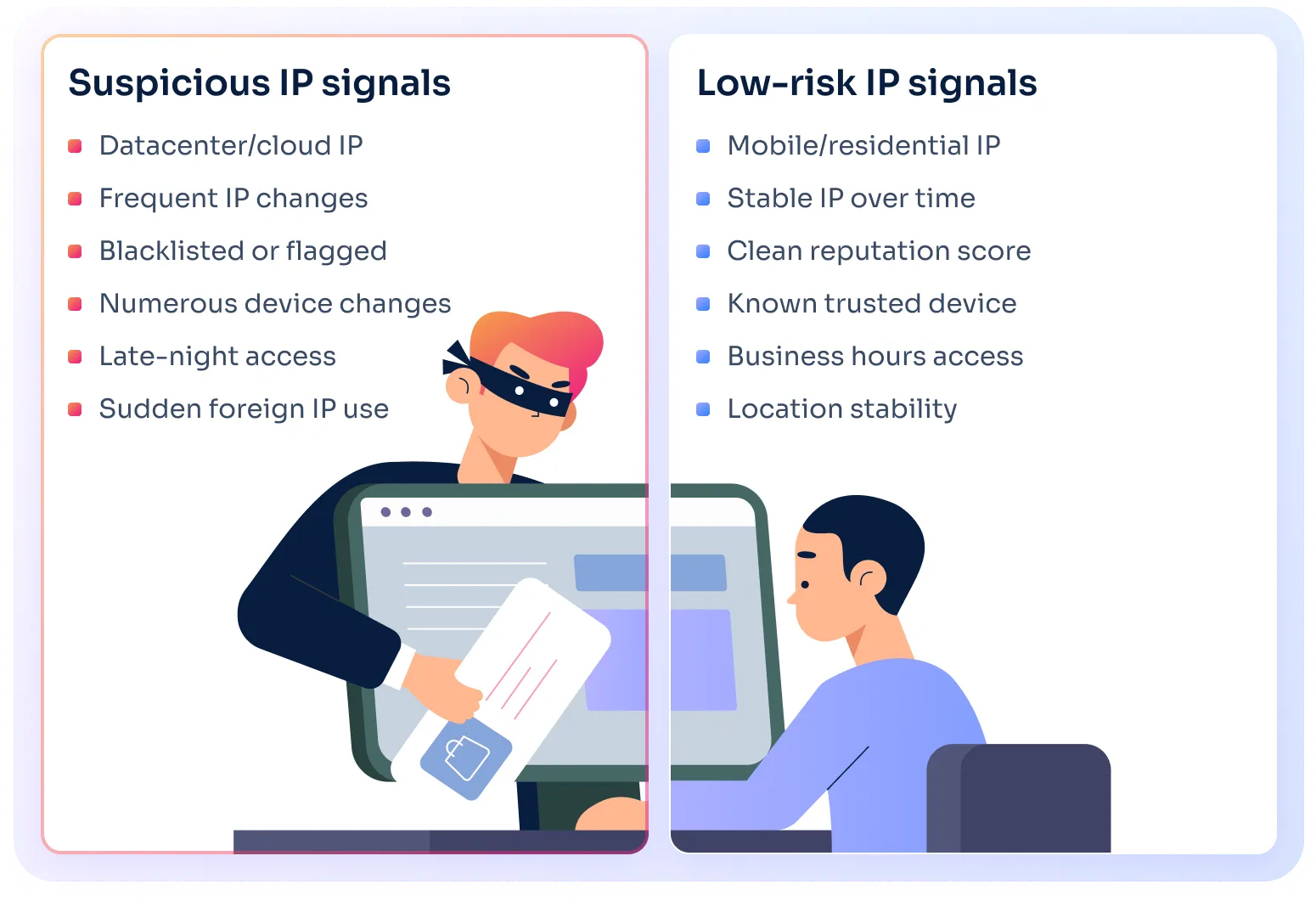
If an IP address is stable over time and tied to a trusted device, it may suggest consistent behavior. Add to that a clean reputation score, no blacklist hits, and a match with declared location.
That way, you’ll get a stronger risk profile, even without a credit file.
IP data also helps segment applicants by risk. For instance, someone applying from a mobile IP in their local city during business hours may seem low risk.
But an application from a datacenter IP in a different country, especially late at night, could raise suspicion. The full context and other supporting signals make all the difference.
By layering them, lenders can make more confident decisions with structured IP risk management. Especially when working with thin-file or first-time borrowers.
#2. Detect IP location lookup anomalies in onboarding
Onboarding is where most fraud attempts begin. IP intelligence can help spot them early.
For example, multiple applications coming from the same IP in a short time are a red flag. So is an IP with a history of abuse or links to open ports and scanners.
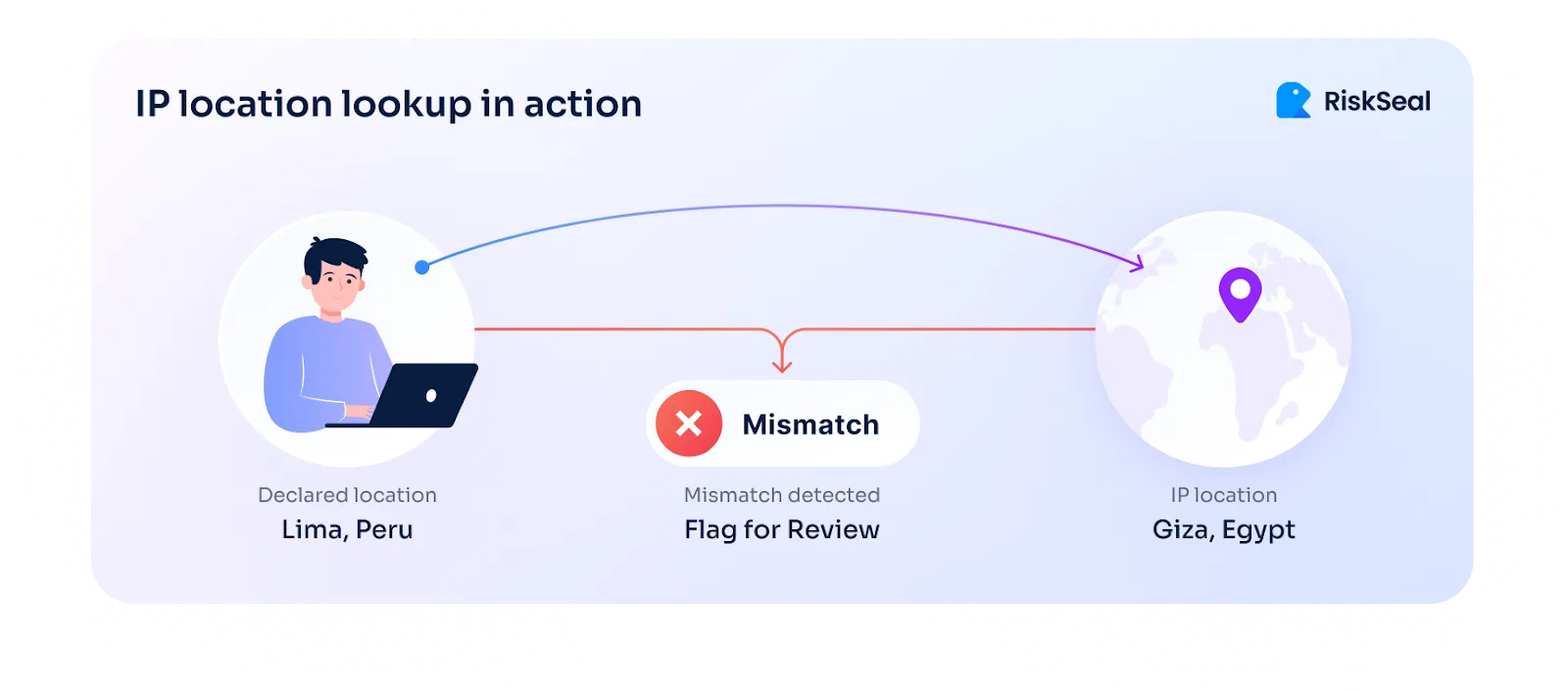
You can also catch location mismatches. If someone says they’re in Peru but the IP shows Egypt, something’s off.
Combined with device and session data, IP analysis helps spot suspicious behavior before it gets further.
This reduces the load on manual reviews and helps automate safer onboarding flows.
#3. Spot subtle geo IP lookup signals beyond fraud
Not all risk looks like classic fraud. Some users may pass identity checks but still pose hidden risks that go undetected.
That’s where subtle IP signals come in.
An applicant might use a residential IP. But if it has a high fraud score, frequent abuse complaints, or belongs to a flagged subnet, that deserves a second look.
Another red flag is erratic behavior from an IP that initially seems safe, such as logins from two distant countries within minutes, which may indicate account sharing or manipulation.
IP intelligence helps uncover hidden patterns that traditional KYC or scoring models might miss. RiskSeal filters out up to 70% of risky applications at the pre-KYC stage, helping risk teams save on KYC budgets.
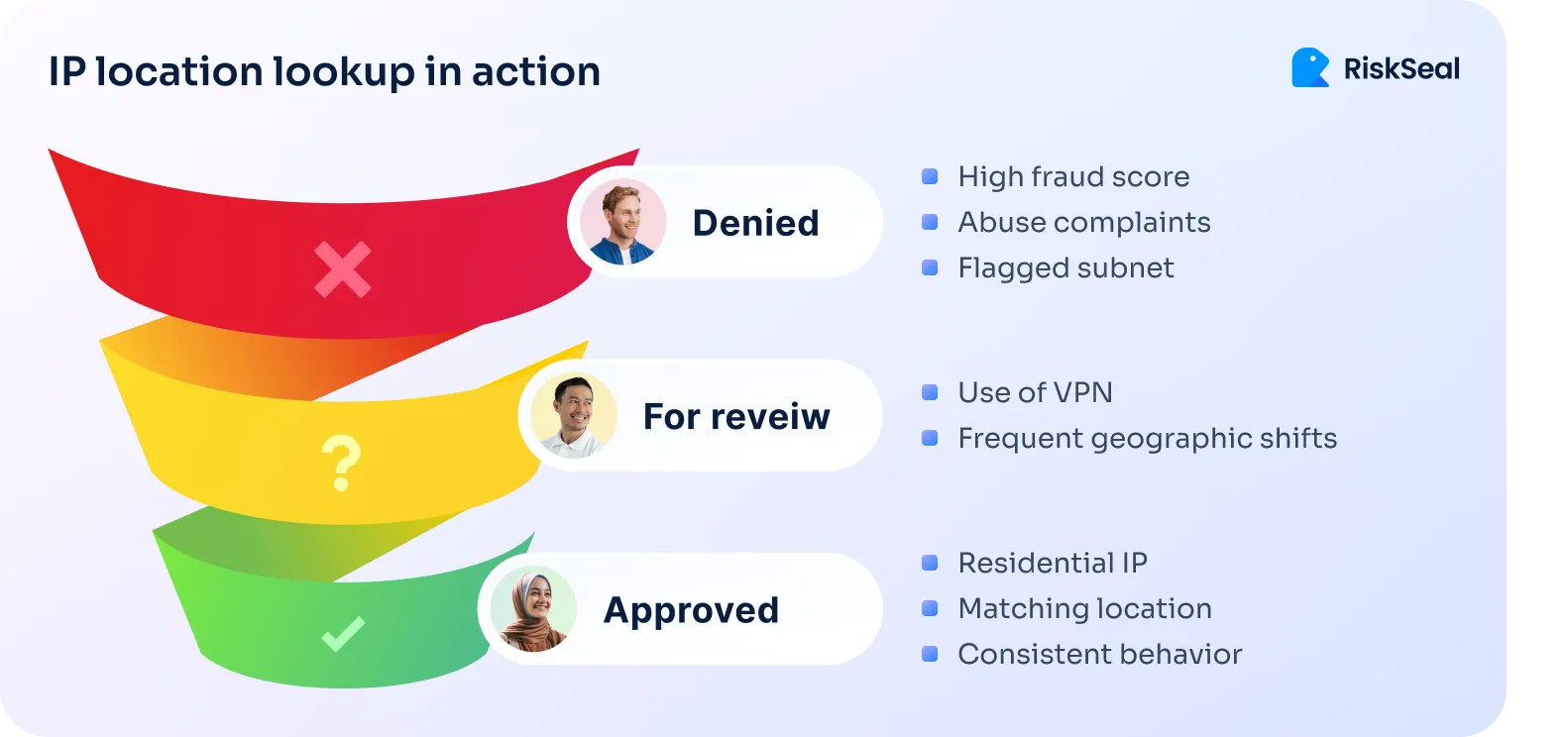
How to use IP intelligence to reduce false positives
IP intelligence is powerful, but it’s not meant to work in isolation.
When used without context, it can lead to blocking the wrong people. That leads to missed opportunities for your lending business.
Avoid overblocking legitimate applicants
A common mistake is treating every unusual result of an IP lookup location as fraud. But not every red flag means risk.
Someone using a VPN might simply be working remotely or protecting their privacy. A mobile IP from a different city might belong to a person traveling for work.
This is why IP analysis should be just one part of your identity and risk checks, not the whole picture. It works best when layered with device info, session behavior, and document verification.
Here are a few common cases where IP signals may look risky, but aren’t:
- VPN usage during remote work or public Wi-Fi use
- IP changes due to mobile network switching
- Datacenter IPs used by fintech-savvy applicants or small business users
- Mismatch in location when traveling or commuting across regions
- Late-night access from shift workers or international applicants
Look at patterns. Is the user behaving consistently? Are other signals clean? If yes, the IP data might just be noise, not risk.
Mind the context behind IP geographic location lookup
Context is key. For example, using an anonymizer doesn't always mean the applicant is hiding something suspicious.
It could be:
- Activists or journalists protecting their identity.
- People in a country with strong internet censorship.
- Privacy-conscious users on Apple’s Private Relay.
- Legitimate applicants using hotel Wi-Fi or shared access.
- Freelancers working abroad but banking in their home country.
- Expats with financial ties in another region.
- Remote employees applying from different jurisdictions.
- Users relying on VPNs or proxies for personal security, not deception.
In these cases, blocking them based only on IP could mean rejecting someone who’s actually low risk.
By combining IP signals with broader behavioral and document data, you can reduce false positives without lowering your fraud defenses.
Using smarter IP geolocation lookup tactics to handle anomalies
Not every anomaly needs to stop an application. Blocking too aggressively can turn away good users and create friction during onboarding.
Instead, it’s better to interpret signals in context and apply flexible responses. Here are three ways to do that effectively:
1. Combine signals, don’t isolate them
An IP mismatch alone isn’t enough. Always review it alongside other indicators like device type, time of access, and past interaction history.
2. Assess risk based on applicant profile
Some groups, like remote workers, foreign students, or frequent travelers, naturally show more variation in IP data. Slight deviations may be expected and don’t always mean risk.
3. Use adaptive flags, not hard blocks
When something feels off, don’t auto-reject. Instead, trigger a soft check:
- Ask for one more document
- Re-run location verification
- Delay the decision for a quick manual review
This approach keeps your fraud defenses strong while giving trustworthy applicants a fair chance to complete onboarding.
How RiskSeal applies IP intelligence
RiskSeal helps lenders use location insights and IP data to verify applicant identities in real time.
Here’s how it works:
The goal isn’t to block people. It’s to flag what’s unusual and let the rest of your decisioning process take it from there.

Download Your Free Resource
Get a practical, easy-to-use reference packed with insights you can apply right away.

Download Your Free Resource
Get a practical, easy-to-use reference packed with insights you can apply right away.




FAQ
What is IP data, and why does it matter in credit scoring?

An IP address is a digital identifier that shows how and where someone connects to the internet. It matters in credit scoring because it reveals useful signals about the applicant’s behavior, environment, and risk level.
What types of information can be extracted from an IP address?

Here’s what can be extracted from IP data:
- Geographic details – country, city, region, ZIP code.
- Connection type – residential, mobile, business, or datacenter.
- ISP or organization info – who owns or operates the network.
- Anonymizer use – VPN, proxy, Tor, or Apple Private Relay.
- Reputation signals – abuse history, blacklists, fraud risk.
- Technical metadata – ASN, subnet, IP version, reverse DNS.
- Behavioral patterns – time of activity, device match, session volume.
All of this can help assess risk quickly and quietly in the background.
How can IP data support credit decisions for thin-file borrowers?

When someone doesn’t have much credit history, IP data helps fill in the gaps.
It can show whether the user is behaving in a trustworthy way. Trustworthy applicant behavior means using a stable IP, logging in from expected places, and not triggering fraud warnings.
How does IP data complement other real-time alternative data sources?

IP data works best when combined with other real-time signals like:
- Device fingerprinting
- Geolocation
- Behavioral patterns (e.g., typing speed, session flow)
- Telco data
- Social media or platform usage
Together, these signals create a fuller picture of the applicant. If one signal looks unusual, the others can provide context. That helps reduce false positives and build smarter, more balanced risk models.
What is reverse IP lookup in credit risk scoring?

Reverse IP lookup in credit risk scoring is the process of identifying the domain or organization associated with an applicant’s IP address. It helps verify if the IP matches the applicant’s claimed identity or location.
For example, if the IP resolves to a known bank or financial institution, it may reinforce the applicant’s financial credibility. Conversely, if the IP points to an unexpected source, such as a hosting provider, VPN, or a region inconsistent with the application, it may raise a red flag.

.svg)
.webp)



.webp)
.webp)