Top 3 Tactics to Detect Identity Theft in Lending
Discover proactive tactics to detect fraud early with alternative data sources and real-time behavioral insights.
.webp)
Identity fraud is getting smarter.
For risk managers, that’s a growing problem. Without new strategies, portfolios suffer, models drift, and default rates climb.
This post discusses the latest loan fraud tricks and explores proactive tactics to help you catch them before they damage your portfolio.
How loan application fraud tactics affect credit portfolios
In 2024, over 50% of banks and fintechs reported a rise in fraud, yet not all fraud hits the credit portfolio the same way. Understanding those differences is key to spotting hidden risks.
Synthetic identity fraud is one of the hardest forms of identity risk, since it shows up as clean credit until the borrower suddenly defaults. These cases often get logged as missed or late payments or thin-file defaults, not as fraud.
Wrong assessment throws off risk segmentation and makes good models look unreliable. Approval metrics rise, while actual portfolio health declines.
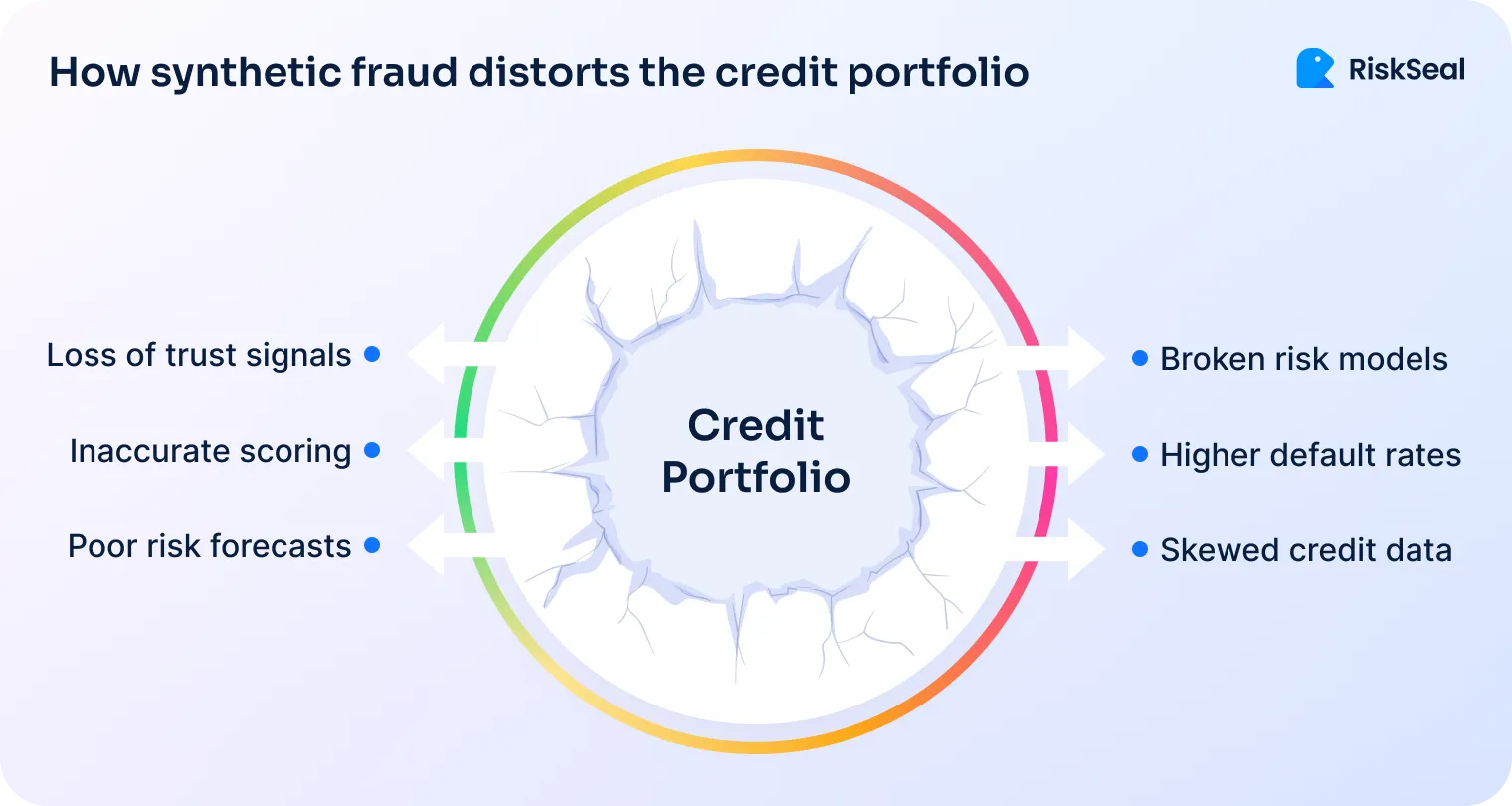
With account takeover (ATO), a fraudster uses a real borrower's account. So, the default gets recorded under the wrong name. The average loss from a successful ATO in banking was about $6,232 in 2024.
ATO losses often get mistaken for normal defaults or missed payments. This leads to tighter lending rules, lower approval rates, and unreliable performance data over time.
Loan application fraud tricks the system into trusting people who never planned to repay. They pass all checks, so their defaults confuse the system.
Without tools to check alternative data beyond KYC, this activity often gets missed. It ends up looking like normal credit risk, making models seem broken.
Tactic #1. Run identity pre-screening before KYC
In 2024, synthetic ID fraud caused $2B in losses on auto loans. But with alternative data, lenders cut loan losses by 15%, according to TransUnion.
Identity pre-screening helps by catching fraud before it hits your credit system.
Where to plug in the pre-screening
Before the soft pull
You don’t need to wait for a bureau check to start spotting risk. Fast checks like email, IP, device, and digital footprint analysis can spot fake applications before you waste time or money.
RiskSeal clients filter out up to 70% of loan applications at this stage, saving KYC budgets.
During auto-decisioning
For digital loans, speed matters. Add pre-screening to your auto-approval to block fraud without slowing down real users.
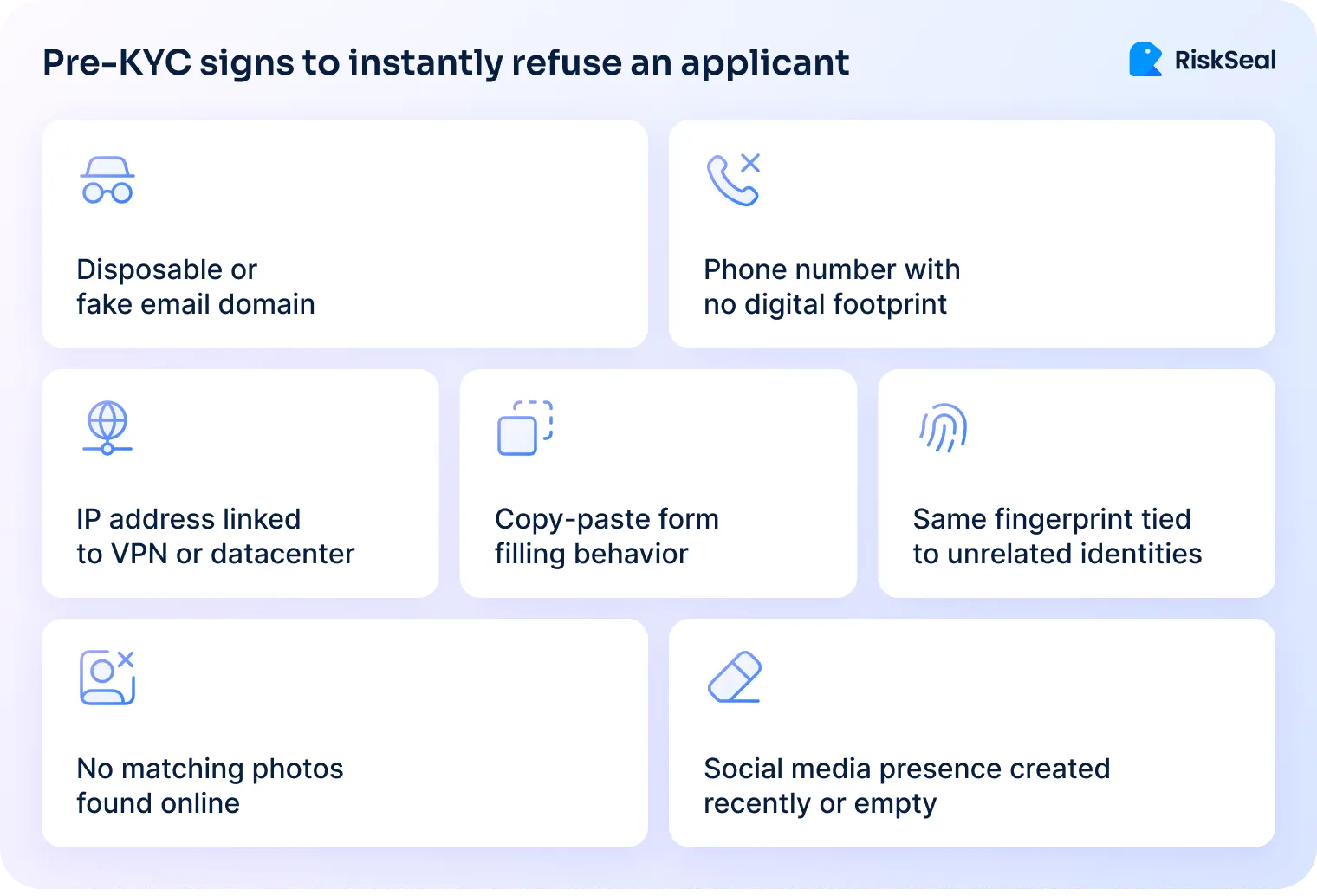
What to screen for
Signal mismatches
Watch out when the email is US-based, the phone number’s from Nigeria, and the IP is pinging from Eastern Europe. Signal mismatches like the use of disposable cell phone numbers are often the first sign of trouble.
Inconsistencies with credit file
If a borrower says they’re in California but their credit file says Texas, something doesn’t add up. Pre-screening helps catch these slips early.
Risky digital behavior
Watch for fast form fills, repeated info from different IPs, or reused forms with different names. These are signs of bots or fraud rings at work.
What to do with the results
Approve, refer, or deny based on signal thresholds
Use these early risk signals to set smart rules. Block the clear fraud, flag the suspicious, and let the rest move smoothly into the next stage.
That way, you're protecting your pipeline without punishing good applicants.
Feed results back into the model for enrichment
Each new solution (approved/rejected/confirmed fraud) gives the system a new experience. These data can be fed back into the model so that it can be trained on real cases and become even more accurate over time.
Tactic #2. Analyze behavior for synthetic borrower detection
Synthetic identities are fake profiles that look real… until they don't. They’re built from bits of real and invented data, and they quietly sneak into credit portfolios.
Catching them early is key to preventing big losses.

Spot synthetic patterns before approval
Thin credit file but high intent behaviors
These profiles often have almost no credit history. Yet, they act like model applicants: fast to apply, accurate, and digitally savvy. That mix is a red flag.
No linked public records
Real people leave a footprint. If there’s no trace in public records – no address, tax info, education, or legal history – it’s likely not a real person.
Suspicious data reuse patterns
Watch for recycled contact details. Fraudsters use the same emails, phones, and devices to create many fake profiles. Repetition reveals the pattern.
Keep an eye on sudden credit limit increases
Credit line max-out and abandonment
A classic move: take the credit, max it out, vanish. This "max-out & vanish" behavior is common in synthetic fraud cases.
First-payment default
Another clear sign of fraud is when the borrower never makes a single payment. If someone defaults right after approval, it’s a strong sign the identity was fake.
Tactic #3. Add post-onboarding controls to catch fraud after approval
Alternative credit scoring and data enrichment help risk teams catch fraud before it causes damage. Even tricky tactics like synthetic identities can be spotted early.
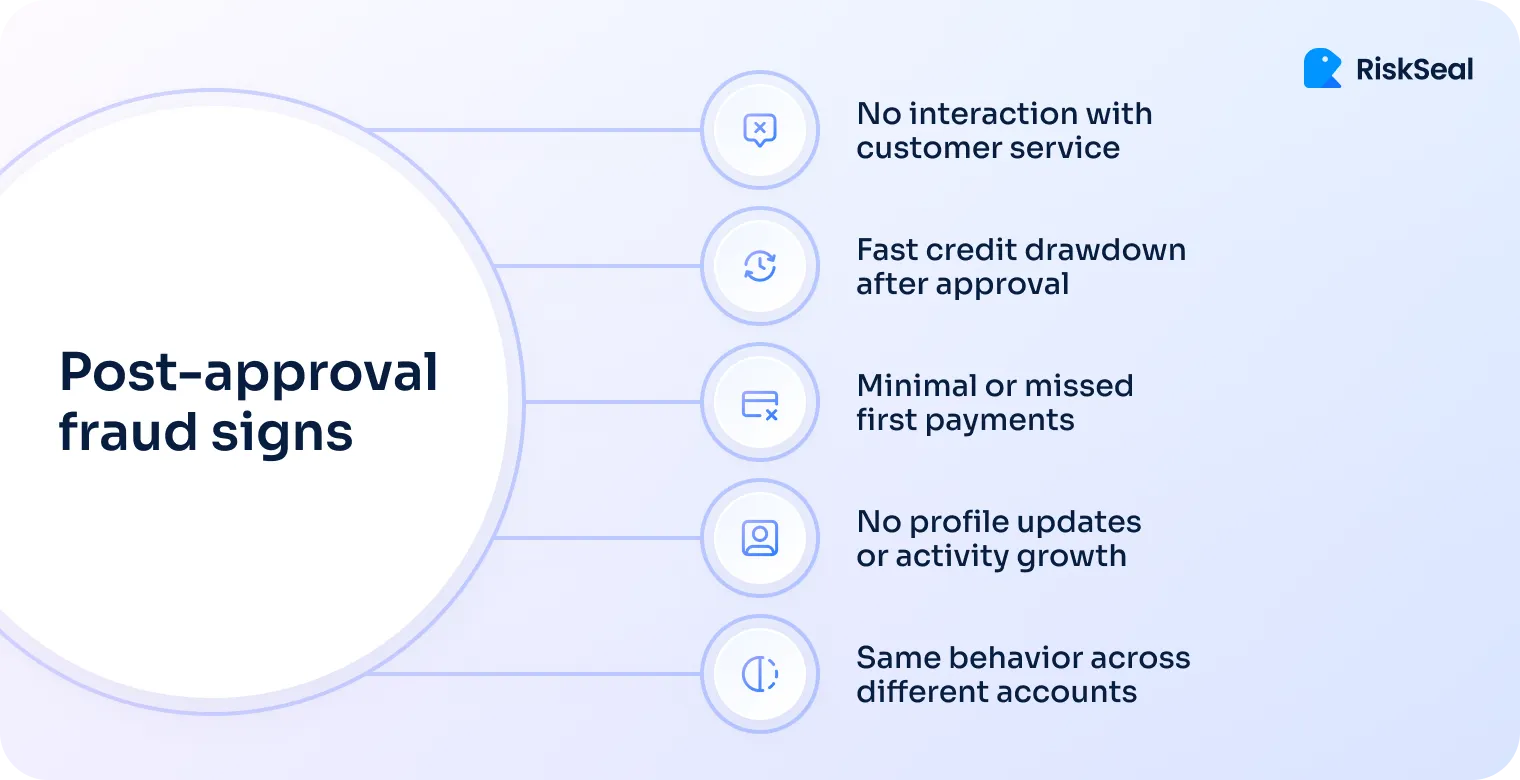
Delay full credit access
Don’t give the full credit limit right after approval. Start small and increase access step by step as the borrower builds trust. It's a simple way to test intent before too much money is at risk.
Identity re-verification on credit line usage
Before large amounts are used, ask the borrower to confirm their identity again. A simple double check can stop synthetic accounts.
Run post-onboarding behavior scoring
Keep an eye on the user right after approval. Track how they pay, how they use the app, and watch for new warning signs. This helps catch fraud that slips through onboarding.
While these tactics offer a strong defense, many lenders still overlook them. Until a real-life fraud crisis forces a rethink.
Real-world case: neobank’s battle with synthetic identity fraud
Can “trustworthy” borrowers suddenly vanish? Yes, and this newly founded neobank learned it the hard way (due to an NDA, we are not revealing its name).
What happened?
The neobank’s team found that 12% of its auto loans issued in Q1 2025 went to synthetic identities. On paper, these borrowers looked flawless: strong credit scores, clean KYC records. But within 90 days, every single one defaulted.
What went wrong?
These profiles sailed through traditional onboarding. The documents looked fine, the credit scores were good, and nothing seemed wrong. But the risk wasn’t in the paperwork; it was in the behavior no one was tracking.
How the fraud was uncovered
The fraud was only discovered when the bank checked against external biometric data. Among the suspicious accounts, 68% had no digital footprint matching their provided documents.
During re-authorization, several red flags appeared:
- Face photos didn’t match the original records.
- Addresses and phone numbers were fake or untraceable.
- Key identifiers were shared across multiple accounts.
- The same personas were recycled with minor tweaks to names and SSNs.
The pattern behind the profiles
Fraudsters reused carefully crafted fake identities just enough to avoid detection. These synthetic borrowers looked like perfect customers at first. Then they maxed out their loans and vanished.
The takeaway
Traditional scoring and KYC completely missed these well-built synthetic profiles. The experience made the bank rethink risk and add alternative data checks earlier in onboarding.
6 reasons why traditional credit models fall short
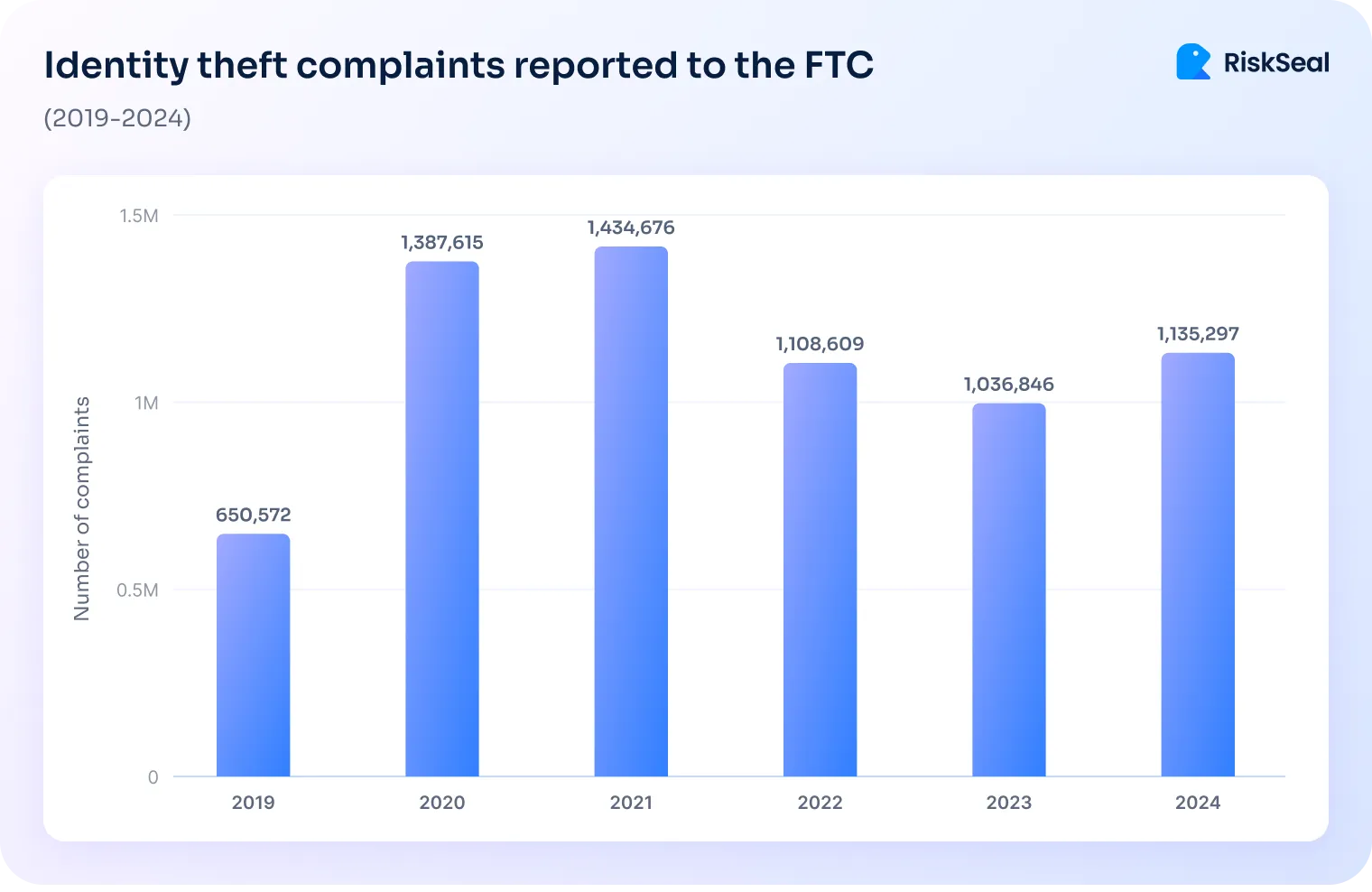
In 2024, U.S. consumers lost $12.7 billion to fraud, with identity theft playing a big role.
Traditional credit models have their place, but in today’s fintech, they simply don’t analyze deep enough. Here’s what they usually miss:
Reason 1. The “identity = intent = risk” assumption is invalid
Older models rely heavily on identity documents to assess someone’s creditworthiness. But just because a person has a valid ID doesn’t mean they’re trustworthy – or even who they claim to be.
Reason 2. Real-time risk signals are missed
Traditional systems rely on fixed data like credit scores or old income statements. That means they can’t spot evolving threats or detect fraud in real time.
Reason 3. Digital behavior is ignored
Checking paperwork is easy, but it doesn't tell the whole story. How someone behaves online gives a much clearer picture of risk.
Reason 4. Thin-file fraud risk often goes unnoticed
Legacy models rely on credit history to assess risk, but thin-file borrowers have little or none. That makes it hard to tell who’s real and who’s a fraudster. As a result, many real thin-file applicants get denied.
Reason 5. Early warnings are spotted late
Most legacy models only flag issues after a loan is approved. They miss early warning signs and end up wasting time onboarding risky borrowers.
Reason 6. AI fraud is smarter than legacy
Fraudsters now use advanced AI to fake identities and trick credit systems. Fixed rules can’t keep up with fast-changing fraud tactics.
So, what should risk managers do now? For a start, look beyond traditional checks. That’s where alternative data analysis comes in.
Rethinking risk intelligence: a new layer for credit decisioning
Proactive risk intelligence gives you deeper insight before you say “yes” to a loan. These smart checks use alternative data to catch risks early, with no delays.
How RiskSeal detects identity fraud in digital lending (before portfolio damage)
Fraudsters don’t apply for loans like normal people, and RiskSeal is built to spot that.
We help lenders detect identity theft before it leads to charge-offs or losses, using a layered approach that combines digital signals, behavioral insights, and third-party data.
What RiskSeal looks at:
Our platform leverages 400+ alternative data points from across 200+ online platforms to build a real-time, multi-dimensional view of every applicant, making it nearly impossible for synthetic identities and fraud rings to slip through.
Want to see how RiskSeal helps risk teams fight identity theft with alternative data? Contact us for a demo.

Download Your Free Resource
Get a practical, easy-to-use reference packed with insights you can apply right away.

Download Your Free Resource
Get a practical, easy-to-use reference packed with insights you can apply right away.




FAQ
What are the early signs of a synthetic borrower in a loan portfolio?

The early signs of a synthetic borrower include a very thin credit file with little or no history. Their behavior often seems too perfect.
They apply fast, fill out forms correctly, and use clean data that looks real. But they usually have no public records: no address, no job history, and no tax data. Later, they might take the full credit, stop paying, and disappear.
That’s when it becomes clear the identity was fake.
What red flags indicate loan application fraud using real data?

Red flags include personal details that don’t match, like different names or addresses across documents. You may also see the same email, phone number, or device used in many applications.
If the IP address doesn’t match the applicant’s location, that’s also suspicious. Filling out the form too quickly can also mean someone is using stolen or fake data.
What weaknesses in traditional credit scoring models enable identity fraud?

Traditional credit models depend too much on fixed data like credit scores, documents, and reported income. They don’t look at real-time behavior or online activity.
This makes it easier for fake or stolen identities to pass through. These models also have trouble judging new or thin-file borrowers. As a result, they may treat fake profiles the same as real ones.
What signal mismatches should risk managers look out for?

Signal mismatches happen when email, phone, and IP address all come from different places. For example, the email may be from the U.S., the phone number from Nigeria, and the IP from Eastern Europe.
This kind of mismatch is a red flag. It may mean the person is hiding their real identity or using fake details. When signals don’t match, it often points to fraud.

.svg)
.webp)




